OpenSSL Testing a Cipher Suite
In this post we’ll look at how to test whether a server supports a certain cipher suite when using TLS.
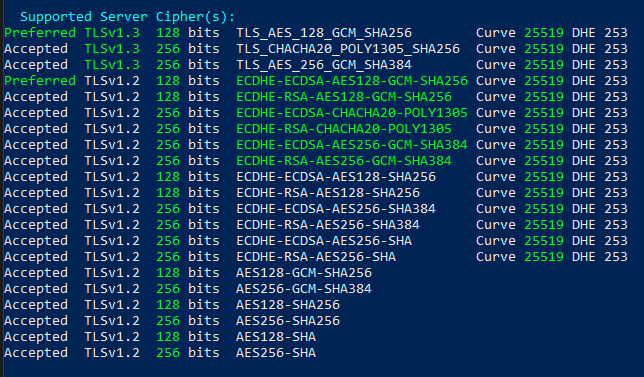
Below we have the SSLScan results of github.com. Let’s see how to manually verify if a certain cipher is valid.
Testing Ciphers for TLSv1.2 & Below
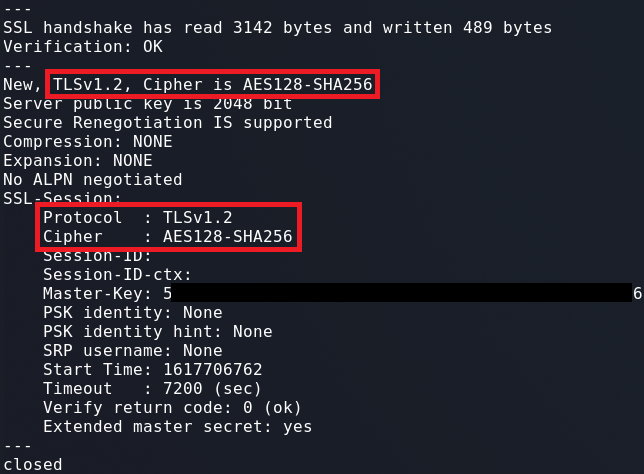
1
openssl s_client -connect github.com:443 -tls1_2 -cipher AES128-SHA256
Testing Other TLS Versions
If we want to test ciphers for other versions of TLS such as v1.0 & v1.1, we need to replace -tls1_2 in the above command with -tls1 and -tls1_1 respectively.
Testing TLSv1.3 Ciphers
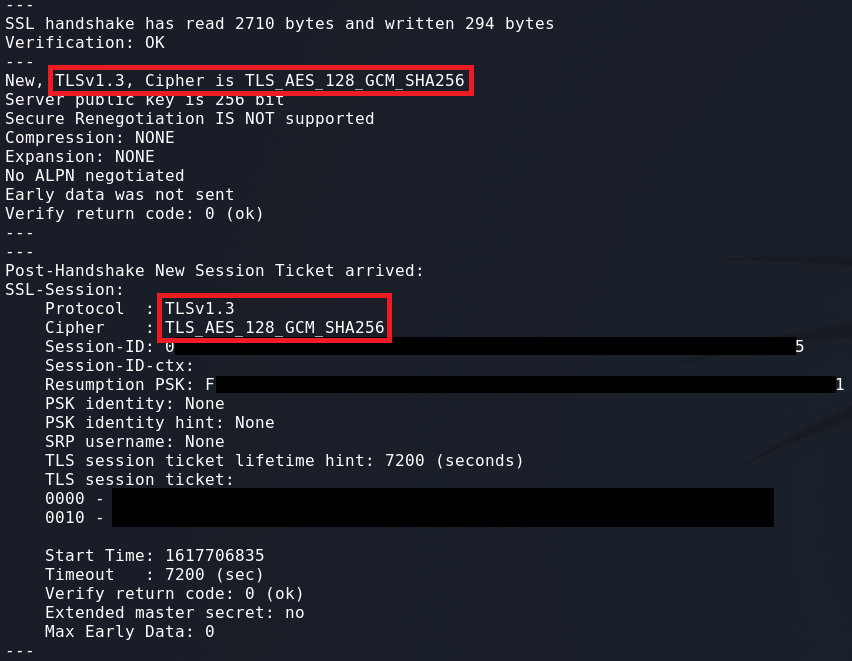
1
openssl s_client -connect github.com:443 -ciphersuites TLS_AES_128_GCM_SHA256
When testing a TLSv1.3 cipher the version flag shouldn’t be required. However, if the wrong version is being used we can specify TLSv1.3 by using the -tls1_3 flag.
Notes
- Make sure to specific a port number at the end of the host name.
- Depending on the version of OpenSSL installed, certain ciphers may or may not be supported.
This post is licensed under CC BY 4.0 by the author.