OpenSSL Testing a Signature Algorithm
In this post we’ll look at how to test whether a server supports a certain signature algorithm when using TLS.
- Testing RSA PKCS1 Signature Algorithm
- Testing RSA PSS RSAE Signature Algorithm
- Testing DSA Signature Algorithm
- Testing ECDSA Signature Algorithm
- Verifying Results
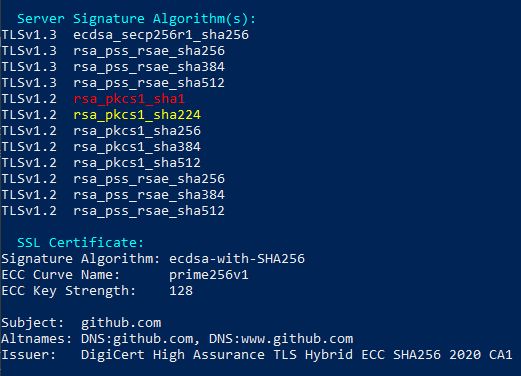
Below we have the SSLScan results of github.com. Let’s see how to verify if a certain signature algorithm is supported by the server.
For all of the below commands SHA256 may be replaced with the desired hash function:
- SHA1
- SHA224
- SHA256
- SHA384
- SHA512
Testing RSA PKCS1
An example algorithm in this category is rsa_pkcs1_sha256:
1
openssl s_client -connect HOST:PORT -sigalgs "RSA+SHA256"
Testing RSA PSS RSAE
An example algorithm in this category is rsa_pss_rsae_sha256:
1
openssl s_client -connect HOST:PORT -sigalgs "RSA-PSS+SHA256"
Testing DSA
An example algorithm in this category is dsa_sha256:
1
openssl s_client -connect HOST:PORT -sigalgs "DSA+SHA256"
Testing ECDSA
An example algorithm in this category is ecdsa_secp256r1_sha256:
1
openssl s_client -connect HOST:PORT -sigalgs "ECDSA+SHA256"
Verifying Results
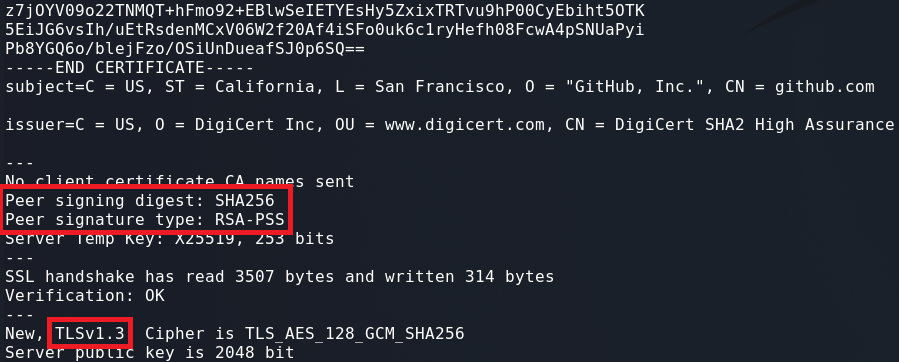
When running one of the above commands you should see the certificate printed out, and below that you should see two fields Peer signing digest: and Peer signature type:. These will be the values that you provided to the -sigalgs parameter.
If the certificate is NOT printed, then the signature algorithm you provided is not supported by the server.
The below image is the output of the following command:
1
openssl s_client -connect github.com:443 -sigalgs "RSA-PSS+SHA256"
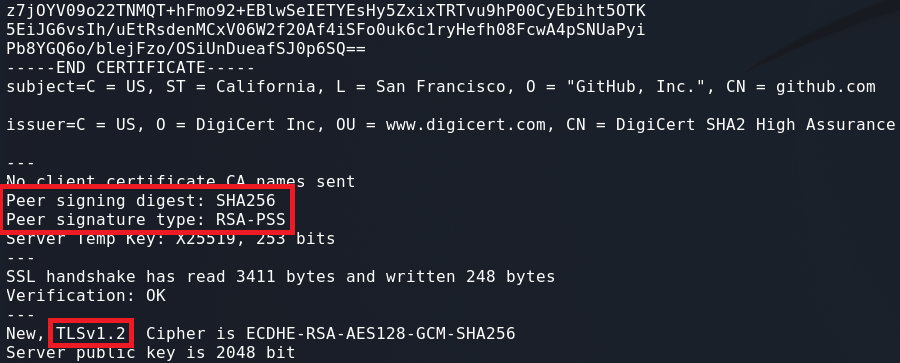
The highest version of TLS supported by the server will be used by default. If you want to test a signature algorithm for TLSv1.2 or TLSv1.3 you can use the flags -tls1_2 and -tls1_3 respectively:
1
openssl s_client -connect github.com:443 -tls1_2 -sigalgs "RSA-PSS+SHA256"
Notes
- Make sure you specify a port number at the end of the host name!
- SSLScan results can be incorrect. Some of the algorithms shown may not work. You can use the aforementioned commands to verify the results.